Dynamic firewall with firewalld
firewalld is a Linux firewall management tool which provides a dynamically managed firewall with support for zones.
firewalld features a two layer design:
-
The core layer: Handling configuration and backends.
-
The D-Bus layer: Interface to various tools which alter and create the firewall configuration.
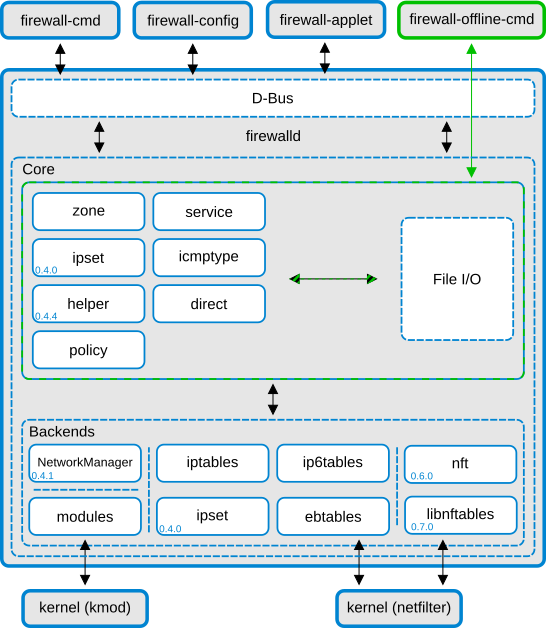
firewalld separates runtime and permanent configurations. The runtime configuration is valid till the next reload or restart, at which time the permanent configuration will be loaded again.
firewalld is a easier-to-use front end of iptables (and other tools). When you change configurations in firewalld, the underlying iptables will be changed accordingly. However, if you decide to stick with firewalld, then refrain from editing iptables directly, unless for some very complex rules.
Basic commands
-
Check firewall status:
firewall-cmd --state -
Reload configuration:
firewall-cmd --reload
Configuration sets
As mentioned above, firewalld has two separate configuration sets: runtime and
permanent. By default, firewall-cmd configures runtime. To configure
permanent, add option --permanent.
Zones
A zone is a set of rules representing a degree of trust. Example zones are
home, work and public. Default zone is public.
-
List configurations in all zones:
firewall-cmd --list-all-zones -
List configurations in a zone:
firewall-cmd --zone=<zone> --list-all -
Get active zones:
firewall-cmd --get-active-zones -
Get default zone:
firewall-cmd --get-default-zone -
Set default zone:
firewall-cmd --set-default-zone=<zone> -
Add an interface to a zone:
firewall-cmd --zone=<zone> --add-interface=<interface>Example
<interface>iseth0.
Services
firewalld can regulate traffic by services. Example services are http, ftp,
squid, ssh. firewalld has pre-defined services, and users can also create
their own custom services.
-
List pre-defined services:
firewall-cmd --get-services -
Add a service in a zone:
firewall-cmd --zone=<zone> --add-service=<service> [ --permanent ] -
Remove a service in a zone:
firewall-cmd --zone=<zone> --remove-service=<service> [ --permanent ]
Ports
It may happen that a service is deployed using non-standard ports. In this case users can configure ports directly.
-
Add a port in a zone:
firewall-cmd --zone=<zone> --add-port=<port>/<proto> [ --permanent ] -
Remove a port in a zone:
firewall-cmd --zone=<zone> --remove-port=<port>/<proto> [ --permanent ]
Example <proto> is tcp or udp.
Port forwarding
-
Add forward from TCP port 80 to 8080:
firewall-cmd --zone=public --add-forward-port=port=80:proto=tcp:toport=8080 -
Add masquerade:
firewall-cmd --zone=public --add-masquerade
Rich rules
Rich rules allow users to create complex firewall rules without the knowledge of iptables syntax.
Direct options
Direct options give users a more direct access to the firewall. This requires users to know basic iptables concepts.
References
- https://en.wikipedia.org/wiki/Firewalld
- https://firewalld.org/
- https://firewalld.org/documentation/concepts.html
- https://www.linode.com/docs/security/firewalls/introduction-to-firewalld-on-centos/
- https://www.digitalocean.com/community/tutorials/how-to-set-up-a-firewall-using-firewalld-on-centos-7
- https://fedoraproject.org/wiki/Firewalld?rd=FirewallD#Direct_options